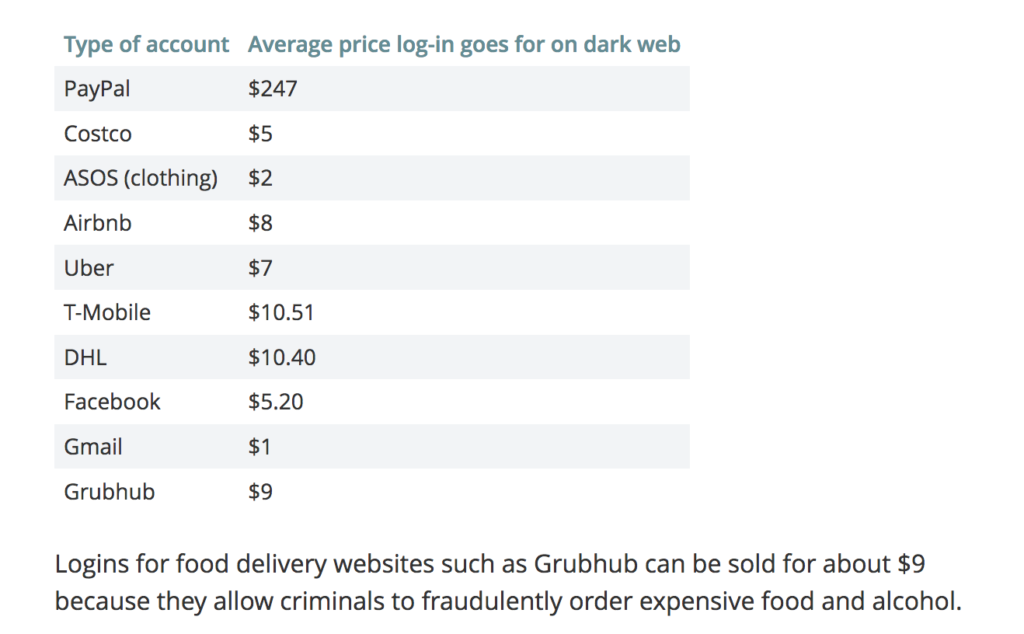
This morning’s Observer column:
You get the picture. This is awfully like the kind of dialogue you would see in a conventional business negotiation. What it shows is what the security expert Ross Anderson has been pointing out for years: that cybercrime has been industrialised and that one can analyse it using the methods and economic concepts that one would use if studying any burgeoning line of business.
In that sense, public discourse about cybercrime and its practitioners is way behind the curve. As Ross and his colleagues have shown, criminals are rational actors, not lone hackers with poor hygiene and a penchant for pizza. They see what they do as a low-risk activity with very high profit margins. And they operate in a networked world in which even large and wealthy companies are still failing to take computer security seriously. The significance of the Colonial hack is its confirmation of cybercrime as a major new industry…