Dedicated to all IT Support persons.
It reminds me of the wonderful instructional film made by the Bell Telephone Company in 1927: “How to use the Dial Telephone”. Archive copy here.

Dedicated to all IT Support persons.
It reminds me of the wonderful instructional film made by the Bell Telephone Company in 1927: “How to use the Dial Telephone”. Archive copy here.

Cambridge on a summer morning with the Cripps Building of St John’s in the distance. The first-floor rooms overlooking the river make up the set where Mervyn King (now Governor of the Bank of England) lived when he was a Research Fellow. Time to start campaigning for a plaque — especially if he manages to keep interest rates down!
One of my favourite webcams is this one. I’ve often wondered about its precise location.
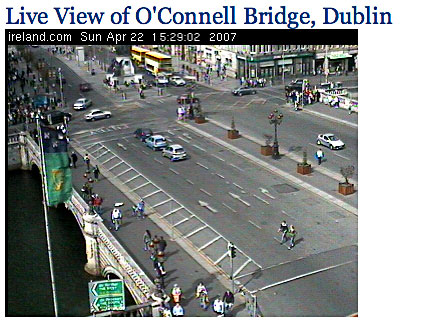
On Friday afternoon I was walking across the bridge on my way to Trinity when I suddenly remembered it and took this picture from a position roughly diagonally across from where I guessed it must be located.

So where is it? My guess is in a window in the top storey of the dark-red brick building on the corner.
Interesting NYT report…
ON YouTube, copyrighted video clips of movies and TV shows are far less popular compared with noncopyrighted material than previously thought, according to a new study.
On their face, the results could have serious implications for YouTube’s owner, Google, and the media companies, most notably Viacom, with which it has been negotiating. But not everyone agrees.
Vidmeter, which tracks the online video business, determined that the clips that were removed for copyright violations — most of them copyrighted by big media companies — comprise just 9 percent of all videos on the site. Even more surprising, the videos that have been removed make up just 6 percent of the total views (vidmeter.com).
The Vidmeter report is here.
This morning’s Observer column…
Wearing his best public-spirited citizen look, Bradford Smith, Microsoft’s general counsel, told the New York Times that Google’s proposed acquisition would ‘combine the two largest distributors of online advertising’ and thus ‘substantially reduce competition in the advertising market on the web’. Between them, Citizen Smith continued, Google and Doubleclick deliver ‘over 80 per cent of the adverts delivered to website publishers, so their combination in a single company has big ramifications’.
Call me Panglossian, but this is encouraging news. One looks forward to General Counsel Smith advising his employer that its 92 per cent control of the market for operating systems also has ‘big ramifications’…
From Saturday’s Herald Trib…
MOSCOW: At their first meeting with journalists since taking over Russia’s largest independent radio news network, the incoming managers had some startling news of their own: From now on, at least 50 per cent of the reports about Russia must be “positive”.
In addition, opposition leaders cannot be mentioned on the air and the United States is to be portrayed as an enemy, journalists employed by the network, Russian News Service, say they were told.
The report goes on to say that:
Parliament is considering extending state control to Internet sites that report news, reflecting the growing importance of Web news as the country becomes more affluent and growing numbers of middle class Russians acquire computers.
Business as usual in the Kremlin, then.

Like most senior executives of western companies, the Microsoft Chairman has been assiduous in sucking up to the Chinese government. Recently he was rewarded with the title of “Honorary Manager” at a ceremony at Beijing Peking University. He also gave a lecture on “China’s Creative Future”. So it was highly fitting that he was greeted by a chap proclaiming the merits of Open Source software. The demonstrator, I need hardly add, was bundled away and is no doubt languishing in gaol.
Thanks to Rex for the link.
Interesting NYT report…
The interesting thing is that the core auction business has gone flat, whereas other businesses they bought — like PayPal, Shopping.com and Skype — seem to be doing quite nicely.
In the first quarter, the number of auction listings increased by only 2 percent, to 588 million. But the total dollar value of merchandise sold in the auctions increased by 14 percent, to $14.28 billion.
In the PayPal unit, revenue was $439 million, up 31 percent. The total volume of payments processed — on which eBay earns a percentage fee — was $11.36 billion, up 30 percent. The fastest-growing part of this business was PayPal Merchant Services, which processes payments on sites other than eBay. That unit handled $4.38 billion in payments, up 51 percent.
PayPal Merchant Services competes directly with the new Google Checkout service, as well as offerings from several banks. Ms. Whitman said eBay had yet to see significant pressure from the Google offering.
Youssef Squali, an analyst for Jefferies & Company, said, “PayPal continues to be the rock star of that business.”
Skype, which earns money largely from fees to connect users to the telephone system, posted revenue of $79 million, up 123 percent. EBay purchased Skype in 2005 for $2.6 billion. “This is a very young business growing very fast,” Ms. Whitman said.
EBay has also increasingly been benefiting from a deal with Yahoo to sell advertising on its site. In the quarter, it had $60.5 million in advertising revenue, up 65 percent.
Well, I suppose the only positive thing is that he didn’t post his video on YouTube…
The student who shot dead at least 30 people at Virginia Tech sent a package to the US TV network NBC News on the day of the shootings, police said…

Clearing out my office, I came on an old Apple external hard drive from the 1980s. Capacity: 20 Megabytes — which is 0.02 Gigabytes. Next to it is a 60 GB iPod. Next to that is a 2GB flash drive. Sobering, isn’t it? The strange thing is that the Apple drive seemed enormous at the time. I remember thinking that if I wrote continuously for 10 years I still wouldn’t have generated enough text to fill it.
But then Bill Gates once said that 640 Kilobytes of RAM ought to be enough for anyone. Or maybe that’s just an urban legend. He’s too smart to have said something that dumb. In the old days, people used to say that you could never be too thin or too rich. Nowadays we say that you can never have too much RAM. Or disk space.
What is true is that Natham Myhrvold (who was for a time Gates’s technical guru) observed that “software is like a gas — it expands to fill the space available”.